These are video games created often in short time frames, with limited development cycles, budgets, and anything else that you need in order to make a decent video game.
But, as with anything, some are worse than others.
So here, we have compiled the top 10 (in no particular order) worst of the worst, the rock bottom, the absolute dredge of them all for you to enjoy.
10. E. T. The Extra Terrestrial (1982, Atari)
While older than most people reading this, this game is often credited as having caused the video game market of 1983 to crash. The game itself was boring and bland, featuring awful graphics (even for its time) and repetitive tasks.
Rumor has it that Atari only gave developers five weeks to develop the game for the Christmas season, which would explain the lack of… well, gameplay in the video game. A huge number of these games were returned, Atari fell into bankruptcy, and, as the legend goes, the remainder of the stock was buried in a New Mexico landfill somewhere.
9. Tomorrow Never Dies (1999)
Remember golden eye 64? Remember how much fun it was to stay up late into the night with three of your best friends, getting mad at each other over picking Oddjob, or someone who grabbed the Golden Gun first? Those were good times. What if the next game released in the 007 franchise was worse in every conceivable way?
Tomorrow Never Dies did away with the first-person view, instead choosing a third-person view. The game only featured a story mode, lacking any multiplayer whatsoever. If they had named this game anything else, it probably would have been fine, but coming hot off the heels of the success that golden eye 64 was, it led many to see this as a downgrade in every way.
8. Marvel’s Avengers (2020)
Crystal Dynamics has done some good work in gaming, don’t get me wrong, but avengers fails in a lot of ways that don’t make sense. The launch of avengers had some serious game-breaking bugs tethered to it, and while most of them have been ironed out over its lifespan, one of the game’s core problems hasn’t been – how content dry and unrewarding it is to play.
The game has a decent story mode, but once you complete it, the only way to progress is to complete multiplayer missions, which are the same boring, repetitive missions that every other games-as-a-service game has. The multiplayer is not fun, and that’s the biggest advertising point of the game. Please just make another Legacy of Kain game, Crystal Dynamics.
7. Saw 2: Flesh and Blood (2010)
“Hey, what if we took a movie that was relatively unique in the horror genre for its interesting puzzles and turned it into a boring action video game?” said the developers of Saw 2: Flesh and Blood. I may be paraphrasing.
The puzzles are boring, the dialogue is boring, you’re having to repeat puzzles often because they do not explain how the puzzles work, and the majority of downtime in between puzzles are filled with quick-timed events. Low amounts of checkpoints means that you’re often having to redo several rooms multiple times.
6. Cat Woman (2004)
Not unlike the movie of the same name, cat woman did extremely poorly with critics and players alike.
Genuinely awful voice acting combined with seemingly malfunctioning camera controls and a mash-one-button-until-you-win combat style made this game an easy one to pass up.
5. Street Fighter: The Movie: The Game (1995)
In the games industry, there’s an unfortunate expectation that a video game made to tie in with a movie is gonna suck. So what happens when a movie is made based on a video game – that is then turned into a video game itself? It’s like an inception of bad video games.
This soulless shell of a game lacks even the most basic things that Street Fighter II had, namely its charm. Seeing Dhalsim stretch-punch or Ryu throw Hadoukens is timeless, but seeing digitized versions of the actors playing these characters doing the same is just painful.
4. James Cameron’s Avatar: The Game (2009)
Picture this: you’ve just seen Avatar in theaters, and it was a wondrous journey through what cinematic effects can look like in 2009. You can’t get over how cool the fight scenes were, how beautiful the landscapes were, or how intricate the sex-hair thing was. So you rush to your local store and immediately spy a copy of Avatar: The Game. Surely it must look just as good, right?
While the game does tackle events prior to the movie, expanding the lore of the world a bit, the graphics looked awful – I can think of a few late-gen PS2 games that looked nicer – the gameplay was bland and repetitive, made worse by the linear paths you have to walk in the game.
3. Evil Dead: Hail to the King
I cannot imagine watching Evil Dead 2having a wonderful time, and then picking this game up and trying to play through it. Hail to the King lacks pretty much everything that made Evil Dead 2 or Army of Darkness work, instead attempting to emulate some action-horror games that had come out before it.
Fixed camera angles are fine in some games, but the game has to be built around them for it to work. This game has problems with enemies swarming you, and you are unable to deal with them due to the camera perspectives.
2. Every Shrek Game That Isn’t Shrek SuperSlam
I don’t really have the energy to go into why all but one of the Shrek games are bad. In short, they’re poorly paced, have game-breaking bugs, are boring and feature repetitive gameplay. Instead, I want to focus on why SuperSlam is a great game.
SuperSlam is technically a bad game, in terms of gameplay and execution. It’s a broken platform/arena fighter, with several characters able to commit to ‘infinite’ combos that generally just make it unfun – in theory.
What makes it fun is that an entire competitive esports community has formed around the broken game, figuring out how the game works within how broken it is. To this day, tournaments are held online, with new players joining in to try to win.
1. Aliens: Colonial Marines (2013)
This one is a pain for me, personally. Alien is such a cool series, with a lot of lore and a lot of good horror sequences – Alien: Isolation is arguably my favorite movie tie-in game because of how oppressive and well-done the horror in that game is. Enter Colonial Marines: a game with broken AI, to the point where Aliens will crab-walk right past you while they try to figure out their pathing, or get caught in level geometry because the developers couldn’t figure out hitbox collision. The graphics were extremely bland for their time, especially when you compare it to the alpha footage that leaked before release, which looked incredible.
What’s worse, however, is the vast number of promises that the developers gave prerelease that were simply not true. It was a giant mess from beginning to end, and Alien fans the world over were truly disappointed.
Written by Junior Miyai on behalf of GLHF.
.










:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/23937422/DEFCON_slide___OverSight_code_snippet.png)



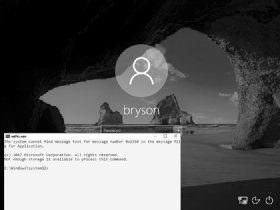
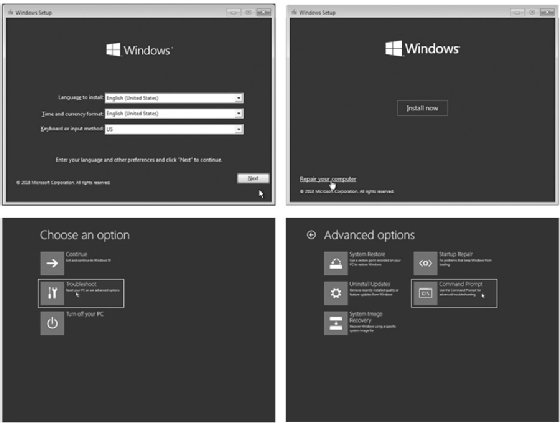
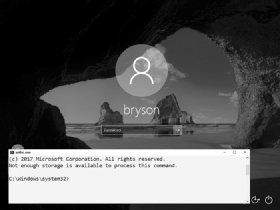
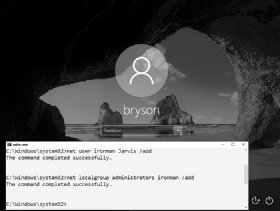 Figure 2-4: We’ve successfully added a user named ironman as an administrator on this computer.
Figure 2-4: We’ve successfully added a user named ironman as an administrator on this computer.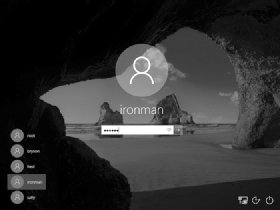

 Bryson Payne
Bryson Payne